Before pressing the Run key we want to set some breakpoints first. Right-click in the Code window of Olly and choose Search For, select All Intermodular Calls. This will bring up the Calls window. Sort the calls by Destination. The problem is that if the code is invalid, the button to submit it is never enabled. Could I use OllyDbg to find what would happen if I were to click the button and then somehow override it? Here's all I know about the program: I do not have access to the source code, nor do I know what language it was written in. OllyDbg is a 32-bit disassembler/debugger for Microsoft Windows binary files. It is shareware and it is available here. The goal today is to provide a tour of OllyDbg and how the tool can be used in reverse engineering software or malware.
It is mostly used for reverse engineering of already developed programs. In other words, we can say that when we have to crack the software developed by any person, we use OllyDbg as a cracker. It is the first choice of any person who intends to do reverse engineering or crack the software. This is because of its being free and easily available.

Requirements
- Windows (for examples only, debuggers exist across platforms)
- A debugger installed: IDA, ollydbg, etc. (ollydbg will be used in examples)
Using Ollydbg To Crack Software
Step 1 Test the Program
First, run the program that you are attempting to reverse engineer and try to activate it with a random key to verify that you need a valid software key to proceed. This is to verify that we can come up with the keys.
Step 2 Run the Program in a Debugger
- Run ollydbg.
- Open up the program you wish to bypass with ollydbg.
- Click the play button to run the program with the debugger attached.
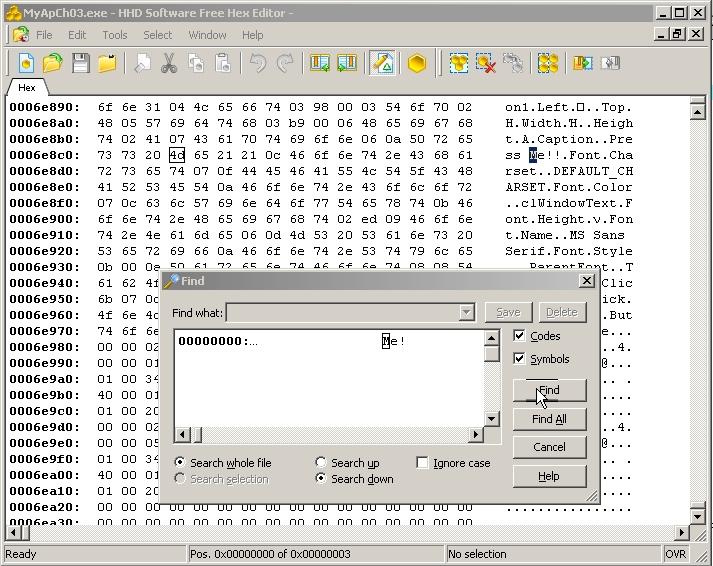
- Right click the CPU window, and click Search For > All intermodular calls.
- Search for high interest DLLs. GETDLGITEMTEXT, will be for dialog boxes, which get called when you try to enter a software key. By stepping into the function with the debugger, we can examine the registration specifically. SENDDLGITEM could be used as well.
- Test to see which one works to break out of the activation loop by right clicking the DLL call and setting a breakpoint for all instances of that call.
- Resume the program and enter any software key you feel like. If the debugger breaks (pauses the program’s execution) after entering your key, then you know you found DLL in step 5.
- Press F8 back in the CPU window to force the next step until you get to the TEST EAX. EAX is the return of a value, which means that a check is being performed here. Upon examination, we can see that the EAX is checking for a number that is not equal to a null value. This means that if it is replaced with anything other than null, it will run.
- Right-click the EAX and change it in hex value to 1, instead of 0.
- Resume the program again, and you will have successfully activated the program.
- And for proof it was registered to me:
Ollydbg Software Crack
Crack software, free download
This works because you are making the process jump from one register and skip the one that verifies the key entered. To exploit the key registration algorithm, keep an eye out for part two of this tutorial on making the key generator. Hooray for assembly!